Android banking trojan Crocodilus has actually released brand-new projects targeting crypto users and banking clients throughout Europe and South America.
Very first identified in March 2025, early Crocodilus samples were mainly minimal to Turkey, where the malware impersonated online gambling establishment apps or spoofed bank apps to take login qualifications.
Current projects reveal it now striking targets in Poland, Spain, Argentina, Brazil, Indonesia, India and the United States, according to findings from ThreatFabric’s Mobile Risk Intelligence (MTI) group.
A project targeting Polish users tapped Facebook Advertisements to promote phony commitment apps. Clicking the advertisement rerouted users to harmful websites, providing a Crocodilus dropper, which bypasses Android 13+ constraints.
Facebook openness information exposed that these advertisements reached countless users in simply one to 2 hours, with a concentrate on audiences over 35.
Related: Microsoft takes legal action versus infostealer Lumma
Crocodilus targets banking and crypto apps
As soon as set up, Crocodilus overlays phony login pages on top of genuine banking and crypto apps. It masqueraded as an internet browser upgrade in Spain, targeting almost all significant banks.
Beyond geographical growth, Crocodilus has actually included brand-new abilities. One significant upgrade is the capability to customize contaminated gadgets’ contact lists, allowing opponents to place contact number identified as “Bank Assistance,” which might be utilized for social engineering attacks.
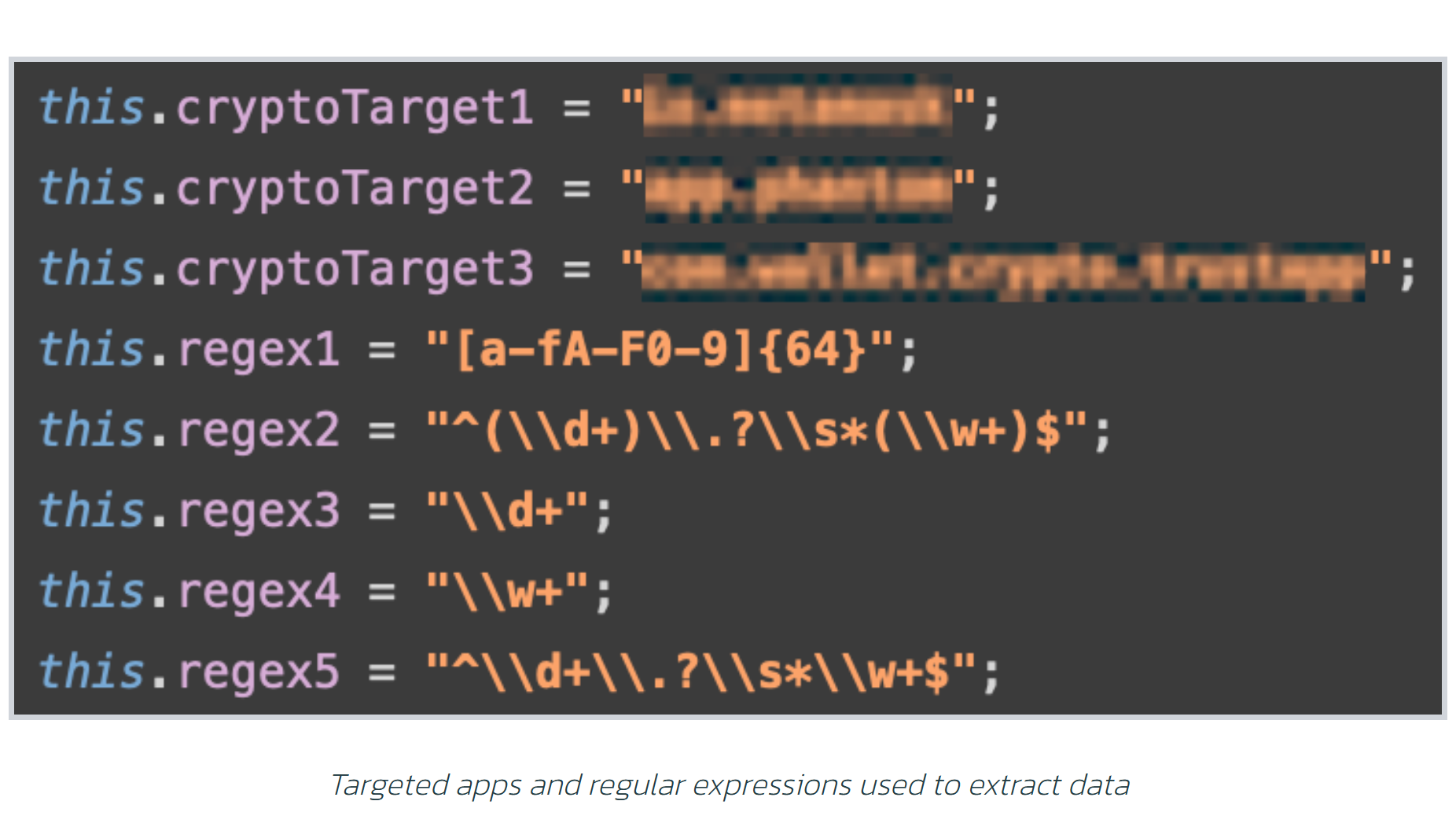
Another essential improvement is an automatic seed expression collector focused on cryptocurrency wallets. The Crocodilus malware can now draw out seed expressions and personal secrets with higher accuracy, feeding opponents pre-processed information for quick account takeovers.
On the other hand, designers have actually reinforced Crocodilus’ defenses through much deeper obfuscation. The current alternative functions loaded code, extra XOR file encryption and deliberately complicated reasoning to withstand reverse engineering.
MTI experts likewise observed smaller sized projects targeting cryptocurrency mining apps and European digital banks.
” Much like its predecessor, the brand-new variation of Crocodilus pays a great deal of attention to cryptocurrency wallet apps,” the report stated. “This variation was geared up with an extra parser, assisting to draw out seed expressions and personal secrets of particular wallets.”
Related: COLDRIVER utilizing brand-new malware to take from Western targets– Google
Crypto drainers offered as malware
In an April 22 report, crypto forensics and compliance company AMLBot exposed that crypto drainers, malware created to take cryptocurrency, have actually ended up being simpler to gain access to as the environment develops into a software-as-a-service company design.
The report exposed that malware spreaders can lease a drainer for just 100-300 USDt (USDT).
On May 19, it was exposed that Chinese printer maker Procolored had actually dispersed Bitcoin-stealing malware together with its main motorists.
Publication: Relocate To Portugal to end up being a crypto digital wanderer– Everyone else is


