Cybersecurity company Hazard Material states it has actually discovered a brand-new household of mobile-device malware that can release a phony overlay for particular apps to deceive Android users into supplying their crypto seed expressions as it takes control of the gadget.
Hazard Material experts stated in a March 28 report that the Crocodilus malware utilizes a screen overlay alerting users to support their crypto wallet secret by a particular due date or threat losing gain access to.
” When a victim supplies a password from the application, the overlay will show a message: Back up your wallet type in the settings within 12 hours. Otherwise, the app will be reset, and you might lose access to your wallet,” Hazard Material stated.
” This social engineering technique guides the victim to browse to their seed expression wallet secret, enabling Crocodilus to collect the text utilizing its ease of access logger.”
Source: Hazard Material
Once the danger stars have the seed expression, they can take total control of the wallet and “drain it totally.”
Hazard Material states in spite of it being a brand-new malware, Crocodilus has all the functions of modern-day banking malware, with overlay attacks, advanced information collecting through screen capture of delicate details such as passwords and remote access to take control of the contaminated gadget.
Preliminary infection happens by accidentally downloading the malware in other software application that bypasses Android 13 and security defenses, according to Hazard Material.
When set up, Crocodilus demands ease of access service to be allowed, which allows the hackers to access to the gadget.
” When approved, the malware links to the command-and-control (C2) server to get guidelines, consisting of the list of target applications and the overlays to be utilized,” Hazard Material stated.
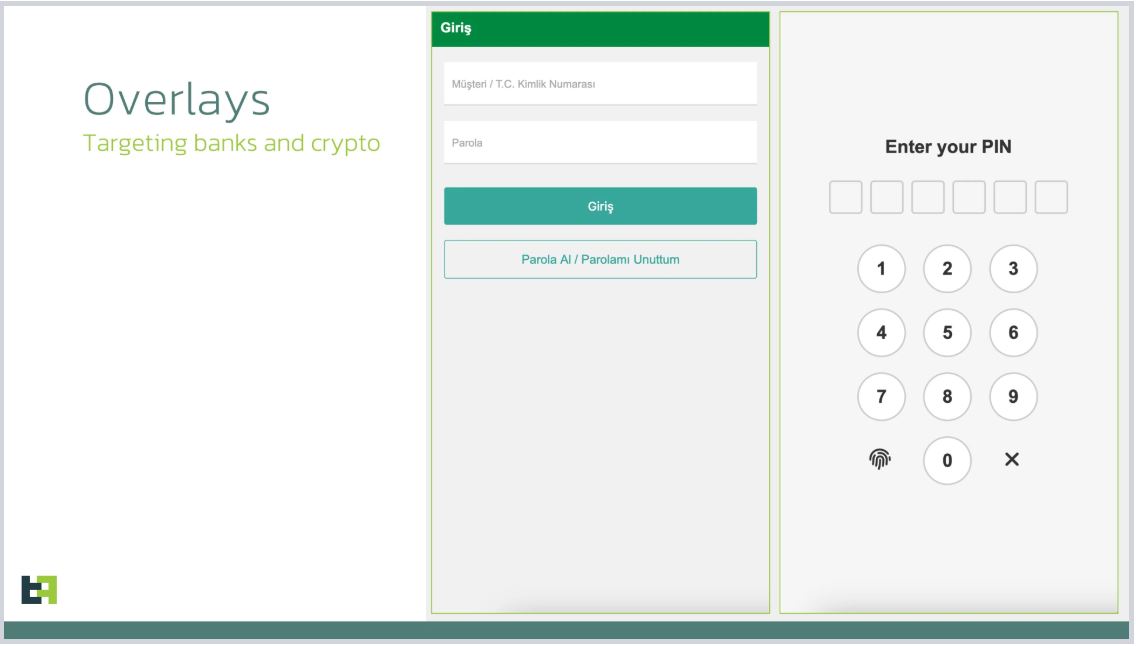
When set up, Crocodilus demands ease of access service to be allowed, approving hackers access to the gadget. Source: Hazard Material
It runs continually, keeping an eye on app launches and showing overlays to obstruct qualifications. When a targeted banking or cryptocurrency app is opened, the phony overlay launches over the leading and mutes the noise while the hackers take control of the gadget.
” With taken PII and qualifications, danger stars can take complete control of a victim’s gadget utilizing integrated remote gain access to, finishing deceptive deals without detection,” Hazard Material stated.
Hazard Fabrix’s Mobile Hazard Intelligence group has actually discovered the malware targets users in Turkey and Spain however stated the scope of usage will likely widen in time.
Related: Be careful of ‘split’ TradingView– it’s a crypto-stealing trojan
They likewise hypothesize the designers might speak Turkish, based upon the notes in the code, and included that a risk star called Sybra or another hacker screening out brand-new software application might be behind the malware.
” The development of the Crocodilus mobile banking Trojan marks a substantial escalation in the elegance and danger level presented by modern-day malware.”
” With its innovative Device-Takeover abilities, push-button control functions, and the implementation of black overlay attacks from its earliest models, Crocodilus shows a level of maturity unusual in recently found risks,” Hazard Material included.
Publication: Absurd ‘Chinese Mint’ crypto rip-off, Japan dives into stablecoins: Asia Express


