North Korea’s IT operatives are moving methods and hiring freelancers to supply proxy identities for remote tasks.
Operatives are calling task candidates on Upwork, Freelancer and GitHub before moving discussions to Telegram or Discord, where they coach them through establishing remote gain access to software application and passing identity confirmations.
In earlier cases, North Korean employees scored remote gigs utilizing made IDs. According to Heiner García, a cyber danger intelligence specialist at Telefónica and a blockchain security scientist, operatives are now preventing those barriers by resolving confirmed users who turn over remote access to their computer systems.
The genuine owners of the identities get just a fifth of the pay, while the remainder of the funds are rerouted to the operatives through cryptocurrencies and even standard checking account. By counting on genuine identities and regional web connections, the operatives can bypass systems created to flag high-risk locations and VPNs.
Inside the progressing recruitment playbook of North Korean IT employees
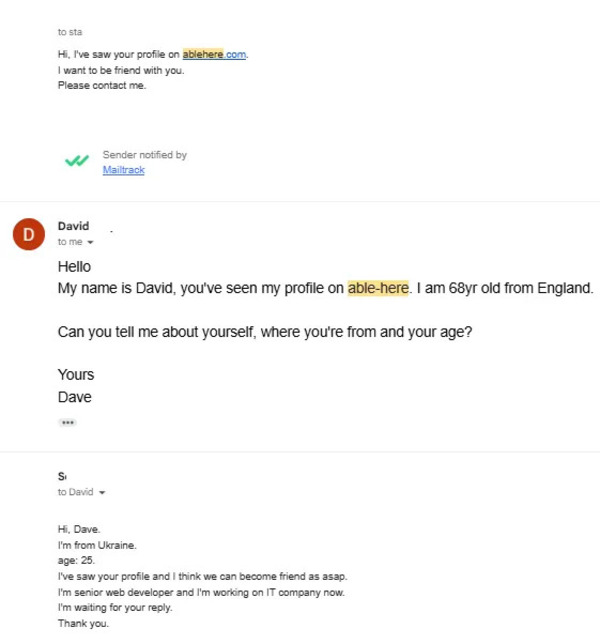
Previously this year, Garcían established a dummy crypto business and, together with Cointelegraph, talked to a thought North Korean operative looking for a remote tech function. The prospect declared to be Japanese, then quickly ended the call when asked to present himself in Japanese.
García continued the discussion in personal messages. The believed personnel asked him to purchase a computer system and supply remote gain access to.
The demand lined up with patterns García would later on come across. Proof connected to suspicious profiles consisted of onboarding discussions, recruitment scripts and identity files “recycled once again and once again.”
Related: North Korean spy mistakes, exposes incorporate phony task interview
Garcían informed Cointelegraph:
They set up AnyDesk or Chrome Remote Desktop and work from the victim’s maker so the platform sees a domestic IP.”
Individuals turning over their computer systems “are victims,” he included. “They are not mindful. They believe they are signing up with a typical subcontracting plan.”
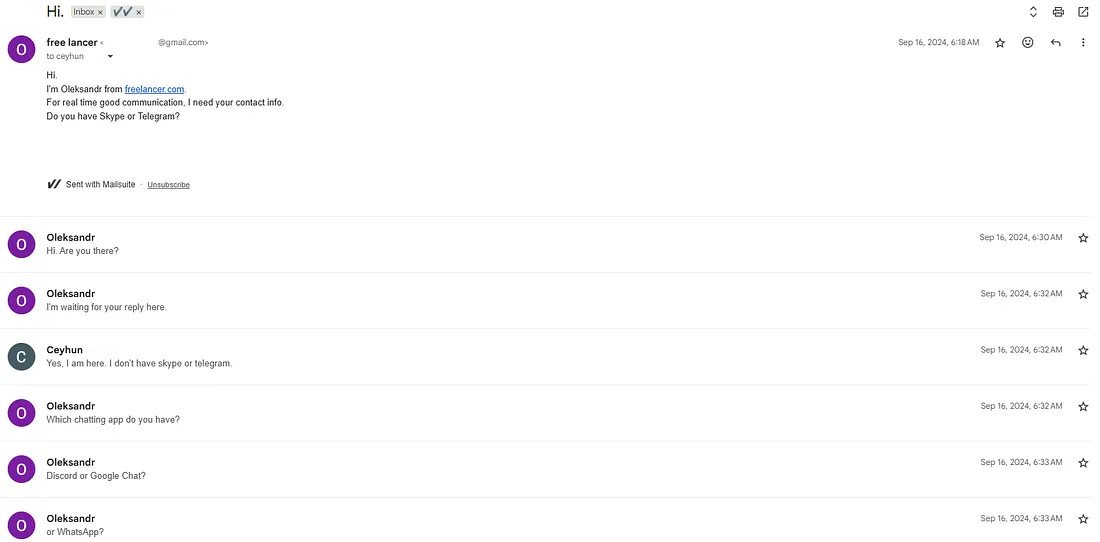
According to talk logs he evaluated, hires ask standard concerns such as “How will we earn money?” and carry out no technical work themselves. They confirm accounts, set up remote-access software application and keep the gadget online while operatives obtain tasks, speak with customers and provide work under their identities.
Though many seem “victims” uninformed of who they’re engaging with, some appear to understand precisely what they are doing.
In August 2024, the United States Department of Justice apprehended Matthew Isaac Knoot of Nashville for running a “laptop computer farm” that permitted North Korean IT employees to look like US-based staff members utilizing taken identities.
More just recently in Arizona, Christina Marie Chapman was sentenced to more than 8 years in jail for hosting a comparable operation that funneled more than $17 million to North Korea.

A recruitment design developed around vulnerability
The most valued employees remain in the United States, Europe and some parts of Asia, where confirmed accounts supply access to high-value business tasks and less geographical constraints. However García likewise observed files coming from people from areas with financial instability, such as Ukraine and Southeast Asia.
” They target low-income individuals. They target susceptible individuals,” García stated. “I even saw them attempting to reach individuals with specials needs.”
North Korea has actually invested years penetrating the tech and crypto markets to create income and gain business grips abroad. The United Nations stated DPRK IT work and crypto theft are presumably moneying the nation’s rocket and weapons programs.
Related: From Sony to Bybit: How Lazarus Group ended up being crypto’s supervillain
García stated the strategy exceeds crypto. In one case he evaluated, a DPRK employee utilized a taken United States identity to provide themselves as a designer from Illinois, bidding on construction-related tasks on Upwork. Their customer got finished preparing work.
In spite of the concentrate on crypto-related laundering, García’s research study discovered that standard monetary channels are likewise being abused. The very same identity-proxy design enables illegal stars to get bank payments under genuine names.
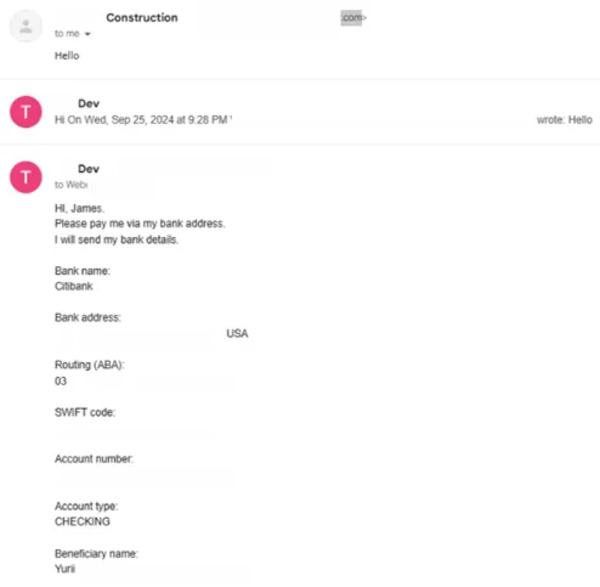
” It’s not just crypto,” García stated. “They do whatever– architecture, style, consumer assistance, whatever they can gain access to.”
Why platforms still have a hard time to identify who’s truly working
Even as working with groups grow more alert to the threat of North Korean operatives protecting remote functions, detection usually shows up just after uncommon habits activates warnings. When an account is jeopardized, the stars pivot to a brand-new identity and keep working.
In one case, after an Upwork profile was suspended for extreme activity, the personnel advised the hire to ask a member of the family to open the next account, according to talk logs evaluated.
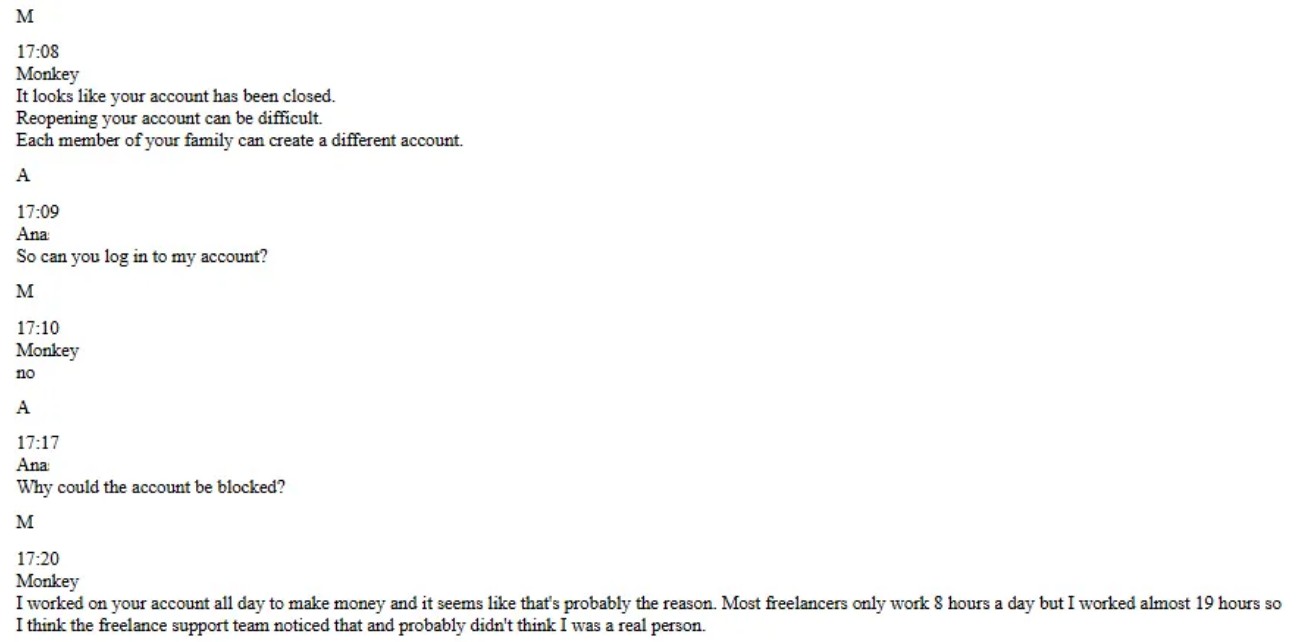
This churn of identities makes both responsibility and attribution hard. The individual whose name and documentation are on the account is typically tricked, while the private really doing the work is running from another nation and is never ever straight noticeable to freelancing platforms or customers.
The strength of this design is that whatever a compliance system can see appearances genuine. The identity is genuine, and the web connection is regional. On paper, the employee fulfills every requirement, however the individual behind the keyboard is somebody completely various.
García stated the clearest warning is any demand to set up remote-access tools or let somebody “work” from your confirmed account. A genuine hiring procedure does not require control of your gadget or identity.
Publication: Bitcoin OG Kyle Chassé is one strike far from a YouTube permaban


