The onchain deals of the exploiter behind the $116 million Balancer hack indicate an advanced star and substantial preparation that might have taken months to manage without leaving a trace, according to brand-new onchain analysis.
The decentralized exchange (DEX) and automated market maker (AMM) Balancer was made use of for around $116 million worth of digital possessions on Monday.
Blockchain information reveals the opponent thoroughly moneyed their account utilizing little 0.1 Ether (ETH) deposits from cryptocurrency mixer Twister Money to prevent detection.
Conor Grogan, director at Coinbase, stated the exploiter had at least 100 ETH kept in Twister Money wise agreements, suggesting possible links to previous hacks.
” Hacker appears knowledgeable: 1. Seeded account through 100 ETH and 0.1 Twister Money deposits. No opsec leakages,” stated Grogan in a Monday X post. “Given that there were no current 100 ETH Twister deposits, most likely that exploiter had funds there from previous exploits.”
Grogan kept in mind that users seldom save such large amounts in personal privacy mixers, even more recommending the opponent’s professionalism.
Balancer provided the exploiter a 20% white hat bounty if the taken funds were returned completely quantity, minus the benefit, by Wednesday.
Related: Balancer audits under examination after $100M+ make use of
” Our group is dealing with leading security scientists to comprehend the problem and will share extra findings and a complete post-mortem as quickly as possible,” composed Balancer in its most current X upgrade on Monday.
Balancer make use of was most advanced attack of 2025: Cyvers
The Balancer make use of is among the “most advanced attacks we have actually seen this year,” according to Deddy Lavid, co-founder and CEO of blockchain security company Cyvers:
” The assaulters bypassed gain access to control layers to control possession balances straight, a vital failure in functional governance instead of core procedure reasoning.”
Lavid stated the attack shows that fixed code audits are no longer enough. Rather, he required constant, real-time tracking to flag suspicious circulations before funds are drained pipes.
Related: CZ sounds alarm as ‘SEAL’ group reveals 60 phony IT employees connected to North Korea
Lazarus Group stopped briefly illegal activity for months ahead of the $1.4 billion Bybit hack
The notorious North Korean Lazarus Group has actually likewise been understood for substantial preparations ahead of their most significant hacks.
According to blockchain analytics firm Chainalysis, illegal activity connected to North Korean cyber stars greatly decreased after July 1, 2024, in spite of a rise in attacks previously that year.
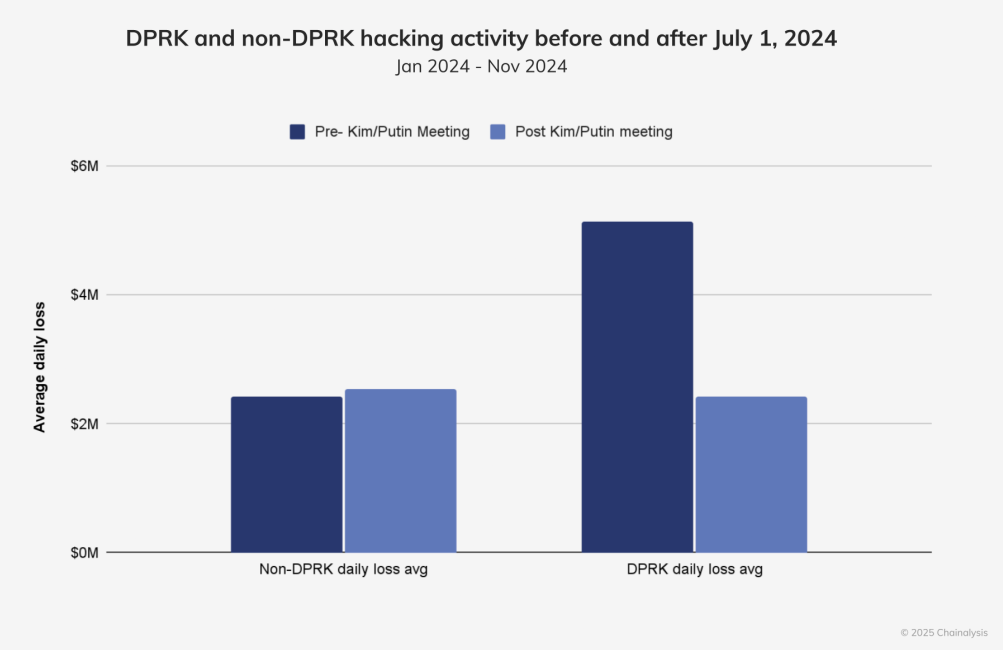
The considerable downturn ahead of the Bybit hack indicated that the state-backed hacking group was “regrouping to pick brand-new targets,” according to Eric Jardine, Chainalysis cybercrimes research study Lead.
” The downturn that we observed might have been a regrouping to pick brand-new targets, probe facilities, or it might have been connected to those geopolitical occasions,” he informed Cointelegraph.
It took the Lazarus Group 10 days to wash 100% of the taken Bybit funds through the decentralized crosschain procedure THORChain, Cointelegraph reported on March 4.
Publication: Coinbase hack reveals the law most likely will not secure you– Here’s why


