A Solana presale occasion came across circulation problems after a bot farm apparently utilized over 1,000 wallets to snipe almost the whole Wet (WET) token sale in seconds.
Hosted through the decentralized exchange aggregator Jupiter, the presale offered out nearly quickly. However real purchasers efficiently had no opportunity to get involved since a single star controlled the presale, according to organizers.
Solana automated market maker (AMM) HumidiFi, the group behind the presale, verified the attack and ditched the launch totally. The group stated it would produce a brand-new token and hold an airdrop to genuine individuals while clearly leaving out the sniper.
” We are producing a brand-new token. All Wetlist and JUP staker purchasers will get a pro-rata airdrop. The sniper is not getting shit,” HumidiFi composed. “We will do a brand-new public sale on Monday.”
Bubblemaps determines declared sniper after tracing over 1,000 wallets
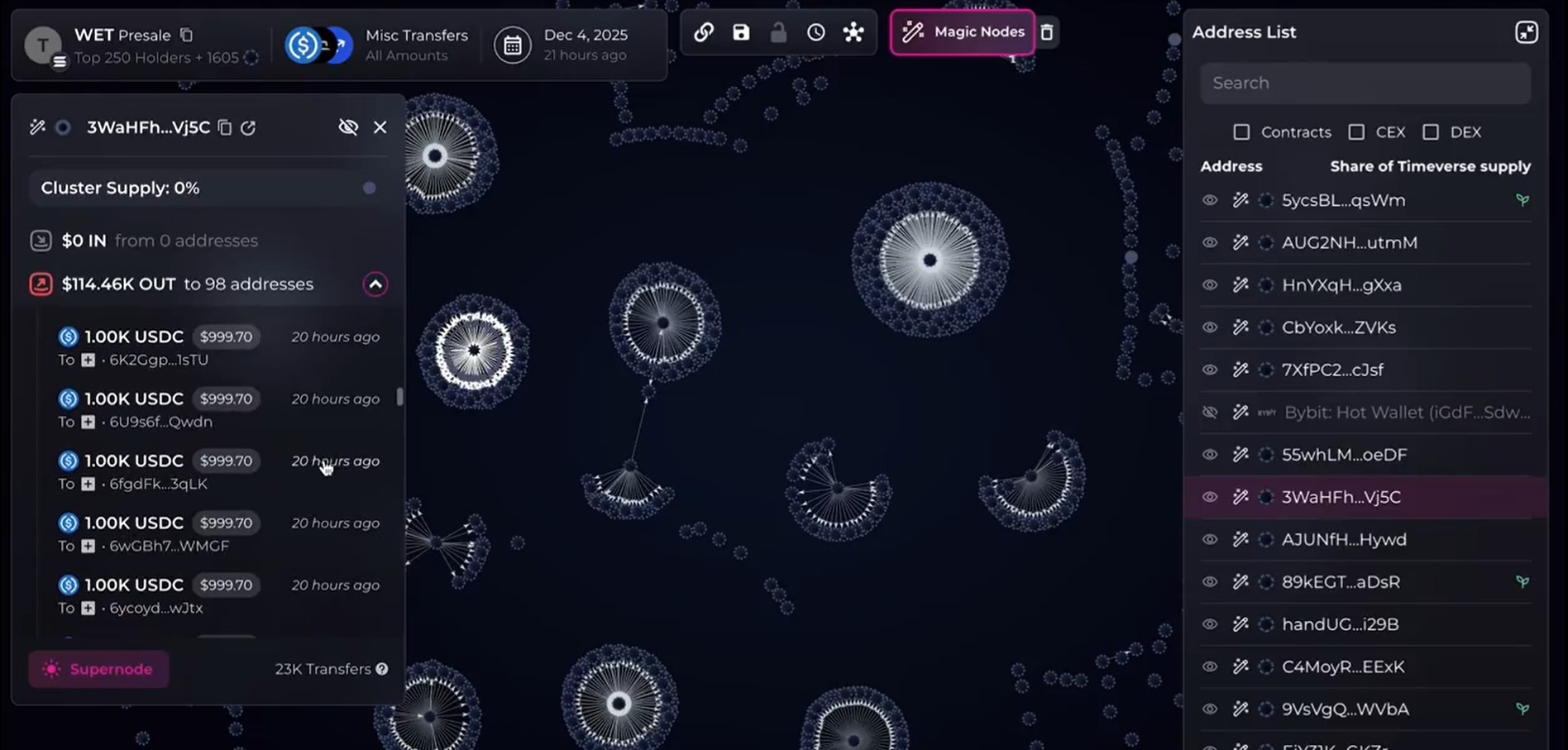
On Friday, the blockchain analytics platform Bubblemaps revealed that it had actually recognized the entity behind the presale attack, having actually observed uncommon wallet clustering throughout the token sale.
In an X thread, the business reported that a minimum of 1,100 out of the 1,530 getting involved wallets showed similar financing and activity patterns, recommending that a single star managed them.
Bubblemaps CEO Nick Vaiman informed Cointelegraph that their group examined presale individuals utilizing their platform and saw patterns, consisting of brand-new wallets without any previous onchain activity, all being moneyed by a handful of wallets.
These likewise gotten financing in a tight time window with comparable Solana (SOL) token quantities.
” In spite of a few of the clusters not linked together onchain, the behavioral resemblances in size, time, and moneying all indicate a single entity,” Vaiman informed Cointelegraph.
Bubblemaps stated that the sniper moneyed countless brand-new wallets from exchanges, which had actually gotten 1,000 USDC (USDC) before the sale.
The analytics business stated among the clusters “slipped,” enabling them to connect the attack to a Twitter manage, “Ramarxyz,” who likewise went on X to request a refund.
Related: Pepe memecoin site made use of, rerouting users to malware: Blockaid
Sybil attacks should be dealt with as a “vital” security danger
The attack follows other Sybil attack events in November, where clusters managed by single entities sniped token materials.
On Nov. 18, a single entity declared 60% of aPriori’s APR token airdrop. On Nov. 26, Edel Finance-linked wallets presumably sniped 30% of their own EDEL tokens. The group’s co-founder rejected that they had actually sniped the supply and declared they had actually put the tokens in a vesting agreement.
Vaiman informed Cointelegraph that Sybil attacks are ending up being more typical in token presales and airdrops. Still, he stated the patterns are “various each time.” He stated that for security, groups ought to carry out Know Your Client (KYC) steps or utilize algorithms to identify sybils.
He stated they might likewise by hand examine presale or airdrop individuals before designating tokens.
” Sybil activity requires to be dealt with as an important security danger to token launches,” Vaiman informed Cointelegraph. “Tasks ought to have committed groups or contract out Sybil detection to experts who can help.”
Publication: Inside a 30,000 phone bot farm taking crypto airdrops from genuine users


